The educational curriculum at this stage considers the demographic and psychological characteristics of children, such as being very young age and their lack of experience. In line with children’s cognitive abilities for this stage, the design is made in a way that aligns with childhood standards, and it focuses on engaging videos and visual content that captivate their interest. The curricula address basic cybersecurity topics such as ways to protect electronic devices, refraining from sharing personal information with strangers, and creating strong passwords. These topics become more expanded and comprehensive as the children’s ages progress.
In order to enhance the attractiveness of the materials offered, and their ability to effectively influence children, the curricula introduce lovely cartoon characters inspired by the Qatari environment, such as a cute robot character, to provide information to children through educational films, posters, and infographic designs, in a way that makes children take these characters as their friends, from whom they derive valuable information and knowledge that they are looking for in the field of cyber security.
-

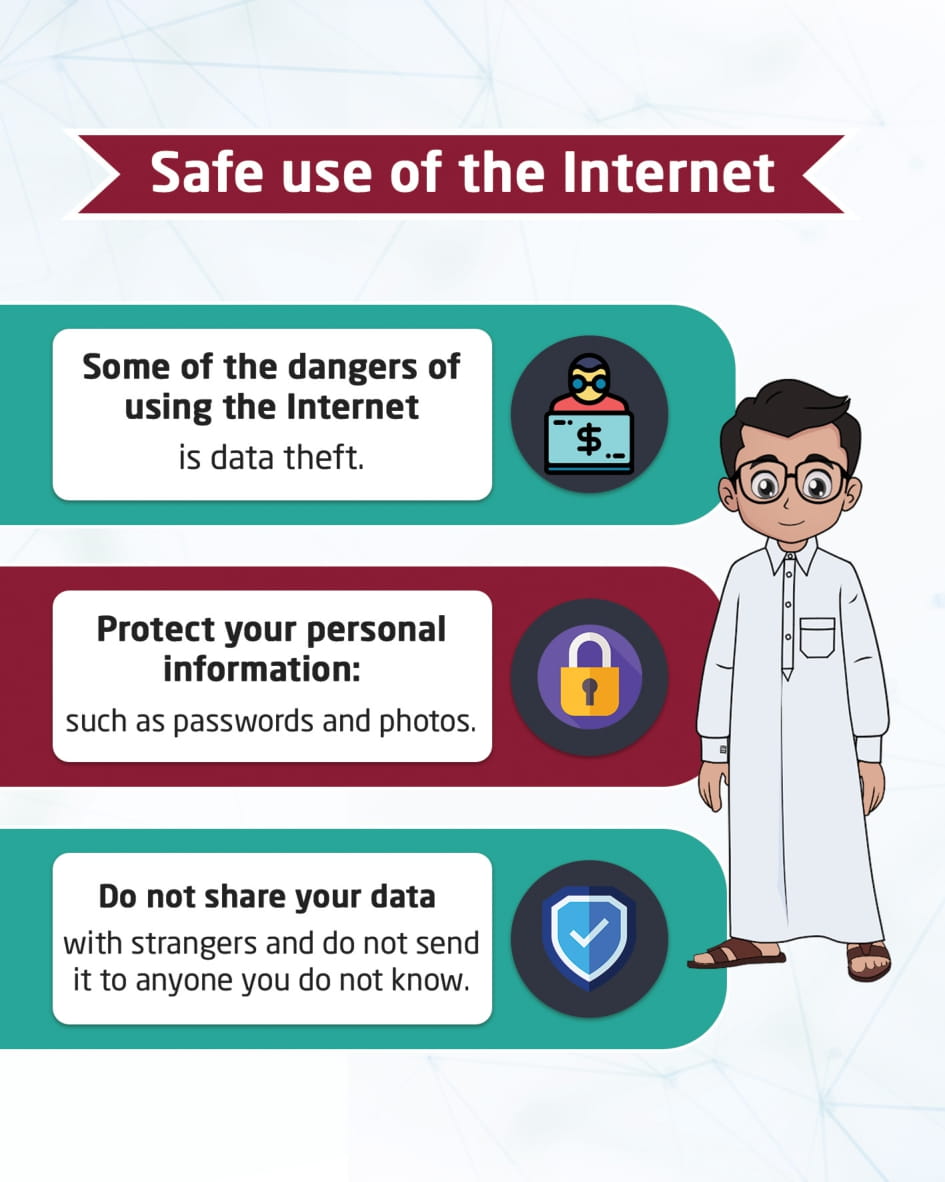
Safe Internet Usage
This visual content discusses Internet safety, protecting personal information like passwords, pictures, and important information, and how to use the Internet safely. like keeping the family's phone numbers and other information private.
WATCH NOW -

Rules for Safe Internet Browsing
This visual content talks about how the user can protect themselves from the risks of using the Internet on their own; in order to prevent anonymous individuals from stealing their data and the significance of providing virus protection software.
WATCH NOW -

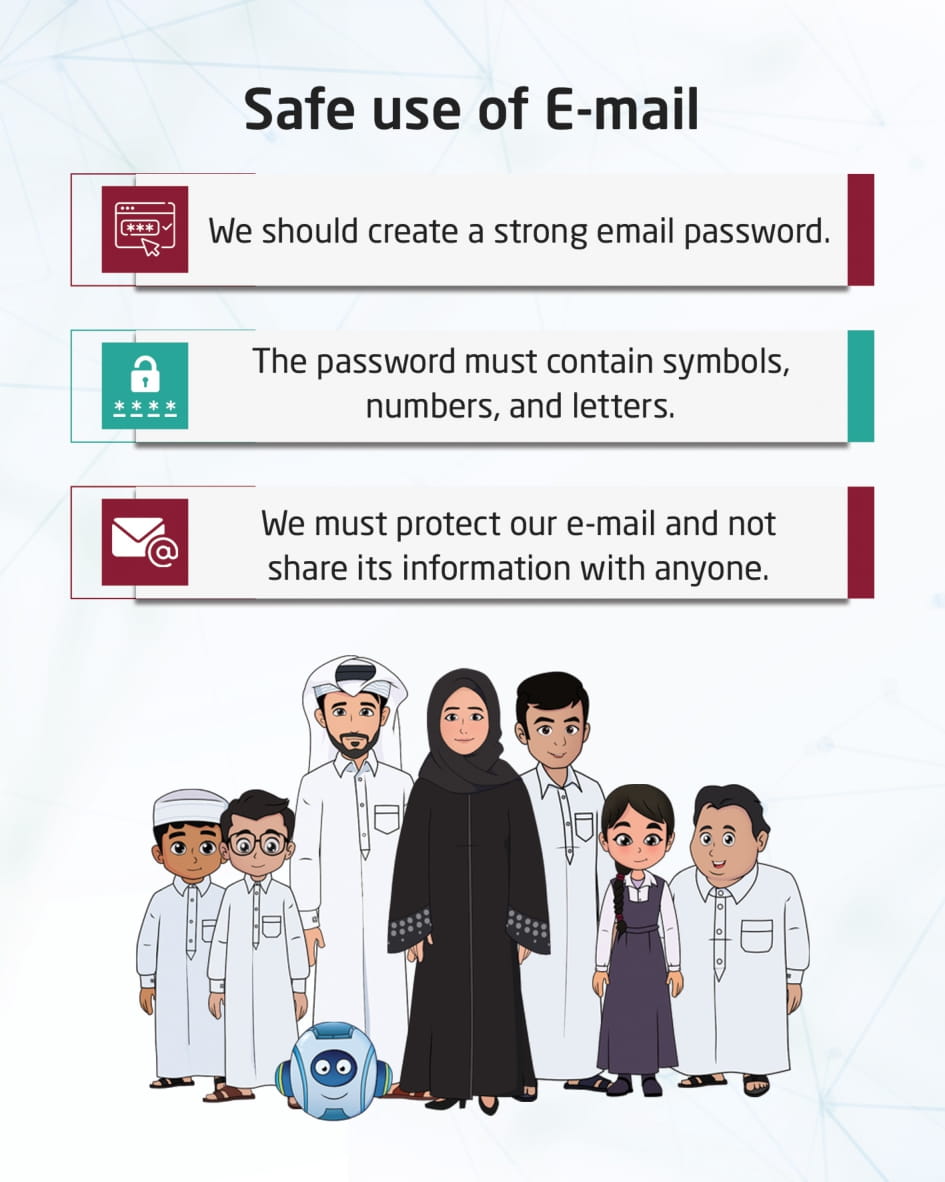
Safe Email Usage
This visual content talks about how you need to be careful when using email, create a hard-to-guess password, and refrain from opening emails from unknown sources or ones that contain advertisements.
WATCH NOW -

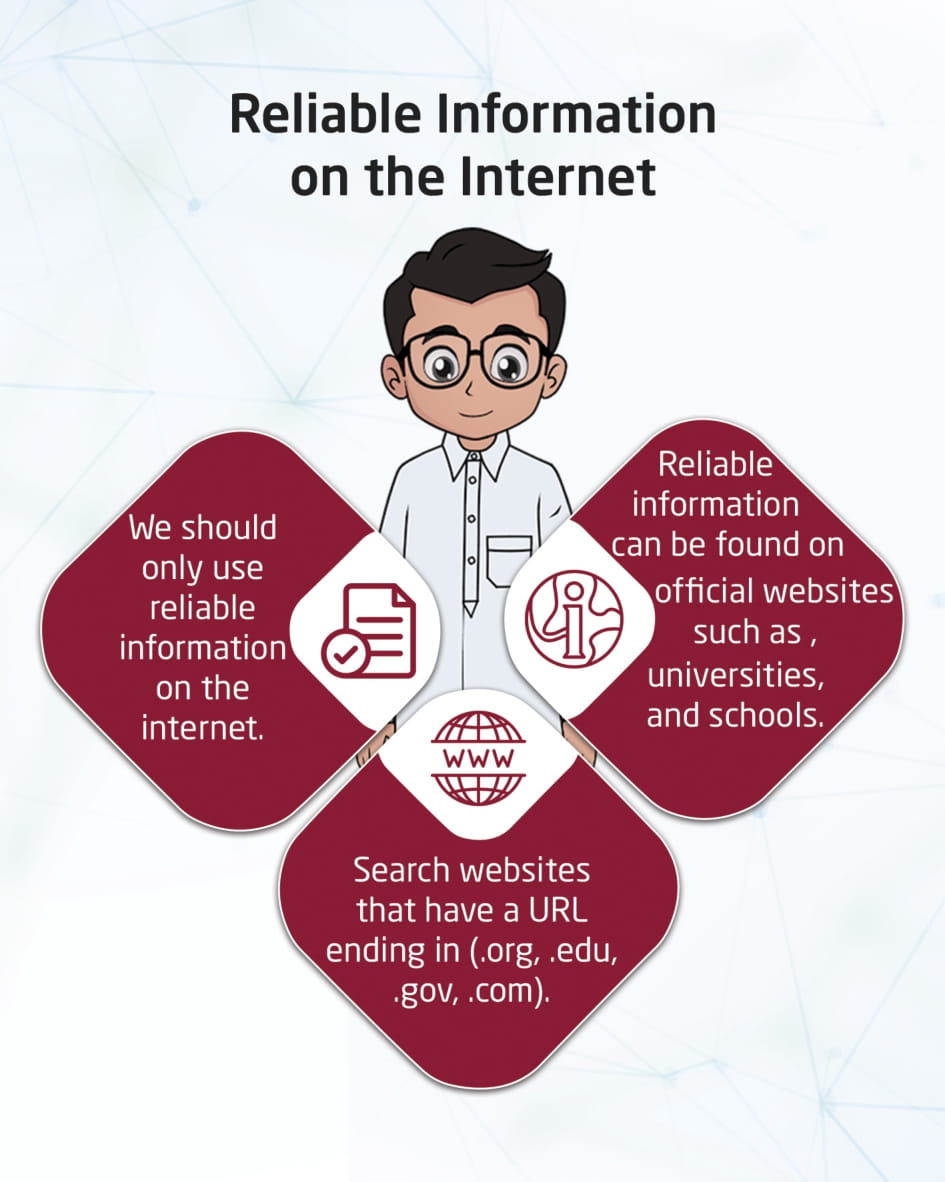
Trusted Information on the Internet
This visual content emphasizes the importance of only using the Internet for information that is reliable. Official and approved websites, such as schools, universities, ministries, and well-known businesses, provide this reliable information.
WATCH NOW -

Trusted Information on the Internet/Part Two (copyrights)
This visual content discusses the significance of citing information sources and identifying the authors of texts and works. respect for copyrights and intellectual property, and emphasizes the importance of following the law when using the Internet; to safeguard both ourselves and others.
WATCH NOW -
Your Health and the Computer
This visual content discusses the significance of health care and warns that prolonged time spent in front of a computer and other technical devices may result in numerous health issues, such as weak vision, eye strain, back pain, and spine curvature.
WATCH NOW -

Your Health and the Computer/Part Two (Social Isolation)
This visual content discusses how social isolation and psychological issues like anxiety, tension, and aggressive behavior can result from prolonged use of electronic devices. And the need to safeguard interpersonal relationships and properly divide time between studying, having fun with friends, and checking electronic devices.
WATCH NOW -

Computer Protection
This visual content discusses the significance of using strong, difficult-to-guess passwords, not sharing passwords with others, and not using common words as passwords to safeguard the computer from hacking
WATCH NOW -

Computer Protection/ Part Two (Software Licenses)
This visual content discusses the significance of using licensed software and the dangers of unauthorized software and information use. not to use or download any untrusted software without authorization; to shield electronic devices from harm and avoid accountability.
WATCH NOW -

Intellectual Property
Before using any electronic game, image, or proprietary material, this visual content discusses the necessity of obtaining permission for it. Additionally, the necessity of respecting intellectual property and adhering to laws to safeguard our rights and those of others.
WATCH NOW -

Intellectual Property/Part Two (Digital Piracy)
This visual content discusses the importance of respecting intellectual property owners’ copyrights to prevent piracy and theft of their innovations. Additionally, issue a warning against infringing copyrights and making unauthorized use of an intellectual property.
WATCH NOW -

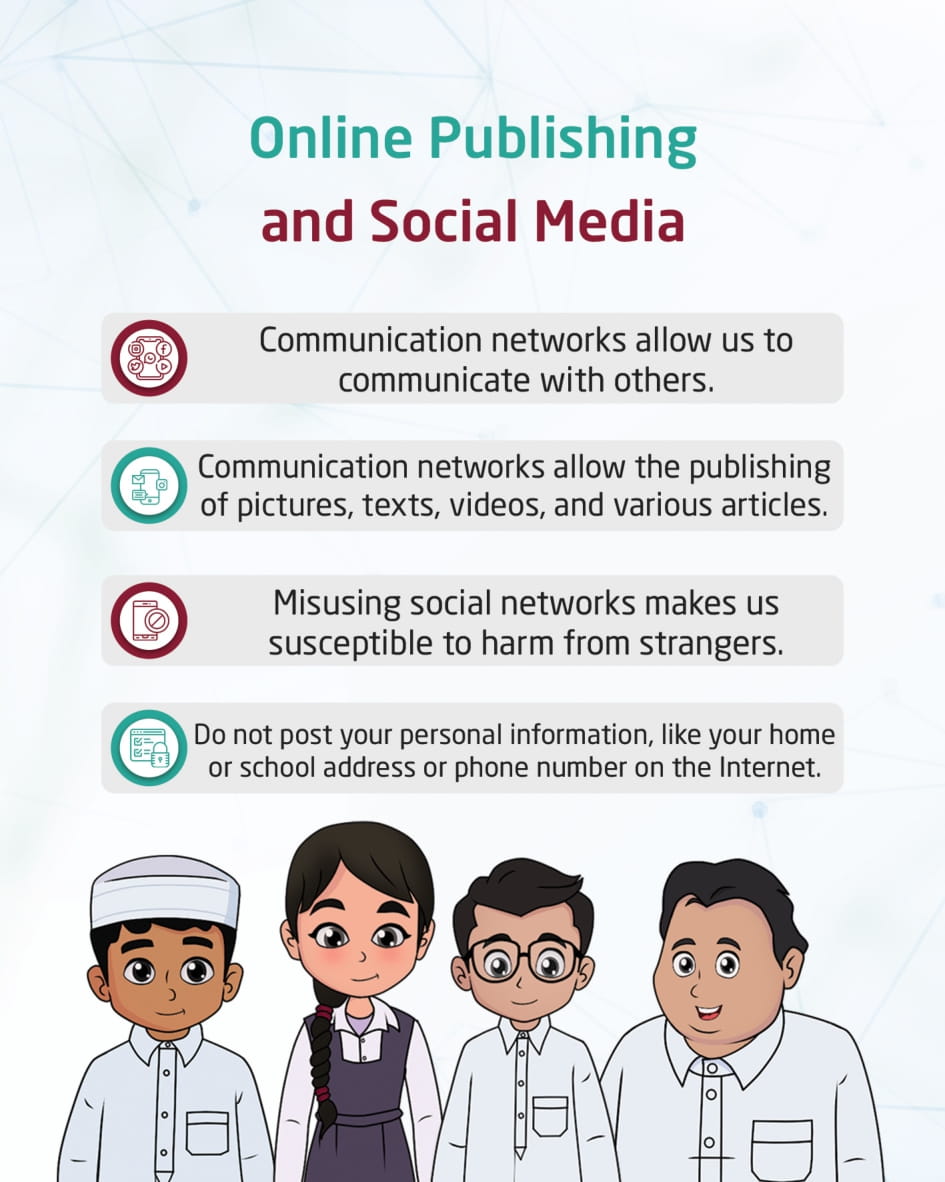
Digital Publishing and Social Media
This visual content discusses the significance of social media and its potential as a wonderful and useful innovation if properly utilized and safety guidelines adhered to. and the need to exercise caution when utilizing these methods, because it might make us vulnerable to fraud and other dangers.
WATCH NOW -

Digital Publishing and Social Media (Cyberbullying)
This visual content discusses the dangers of cyberbullying and cautions against speaking, publishing images or clips of visual content, or making offensive comments on other people’s pages. And not to share any posts that are inappropriate or could harm other people’s mental health.
WATCH NOW