In this stage, topics related to cloud computing, how to deal with it, the basics of file protection, information about electronic attacks, phishing, threats and how to deal it, and other relevant information are introduced in an age-appropriate way that considers the children's and adolescents' maturity and capability in analyze and deduction.
-
Evaluating Online information Sources
This visual content talks about how to evaluate information sources on the Internet through 6 basic criteria for evaluating electronic resources, which are: responsible party, purpose, coverage, accuracy, validity, objectivity, and credibility.
WATCH NOW -

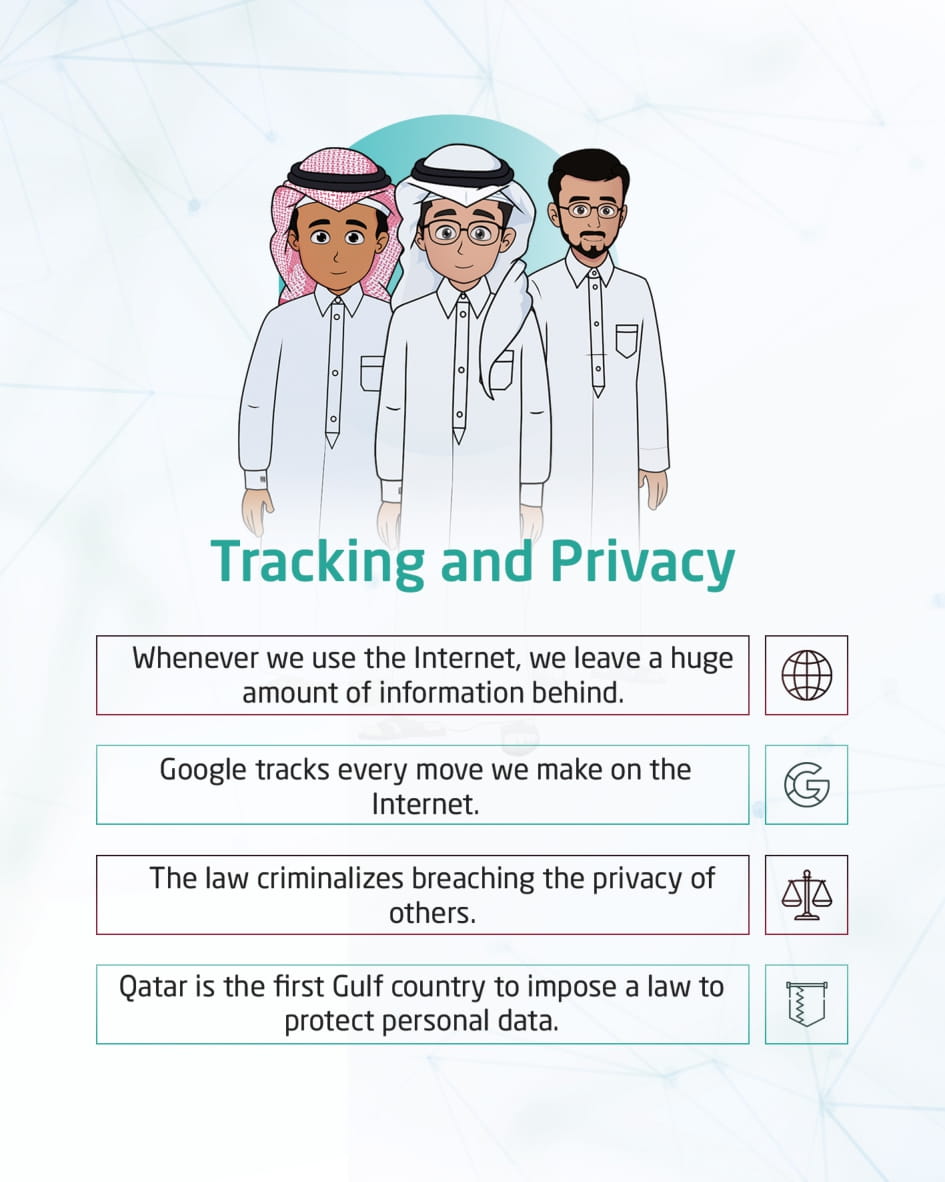
Tracking and privacy
This visual content talks about the online data tracking policy, and that the Internet user leaves behind a huge amount of information since Google tracks every user’s movement on the Internet. It points out that Qatar is the first Gulf country to impose a law to protect personal data.
WATCH NOW -

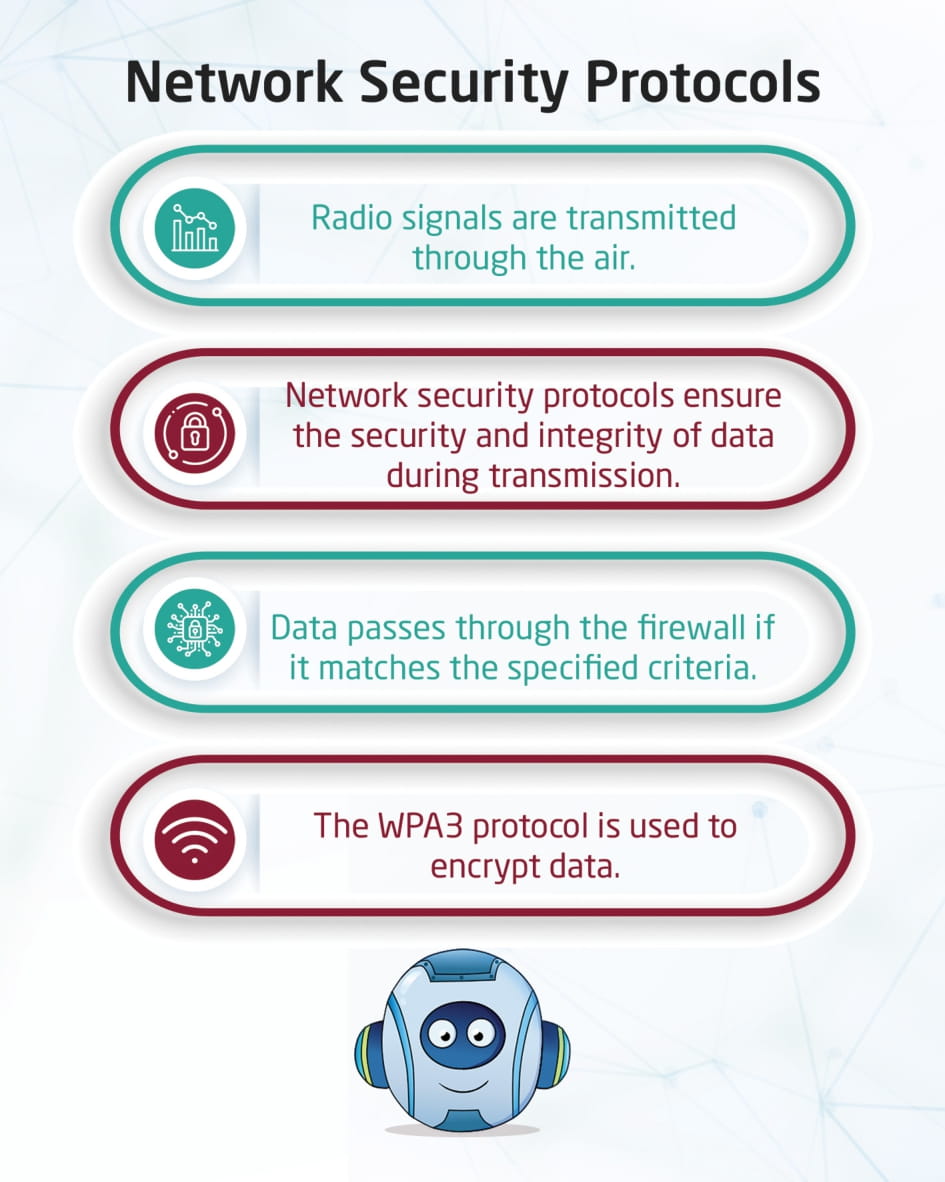
Network Security Protocols
This visual content talks about network security, and the importance of maintaining networks from the risks of external attacks, by using network security protocols that ensure the security and integrity of data during transmission over the network, and the firewall allows data to pass if it matches the permissible standards.
WATCH NOW -

Security and Usability
The security mechanisms for data are discussed in this visual content. by being careful when dealing with spam, not opening emails from an unknown sender, creating strong passwords that are hard to guess, constantly changing them, and not sharing passwords with anyone.
WATCH NOW -

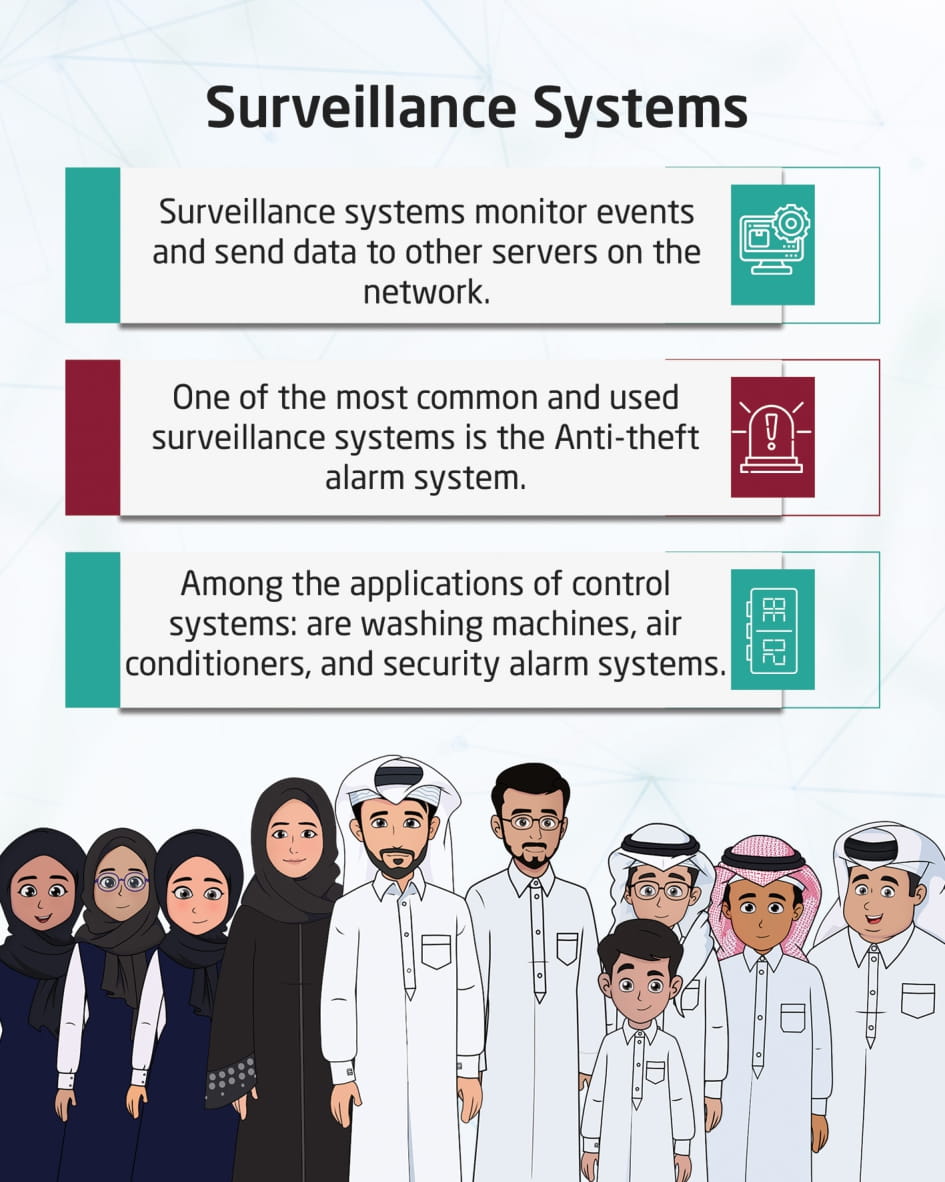
Surveillance Systems
This visual content is about monitoring systems that are designed to monitor certain events or things, and provide monitoring data to other servers or devices on the Internet. One of the most common surveillance systems is: Theft alarm system. Examples of applications of control systems in our lives are: washing machines, air conditioners, and alarm systems.
WATCH NOW -
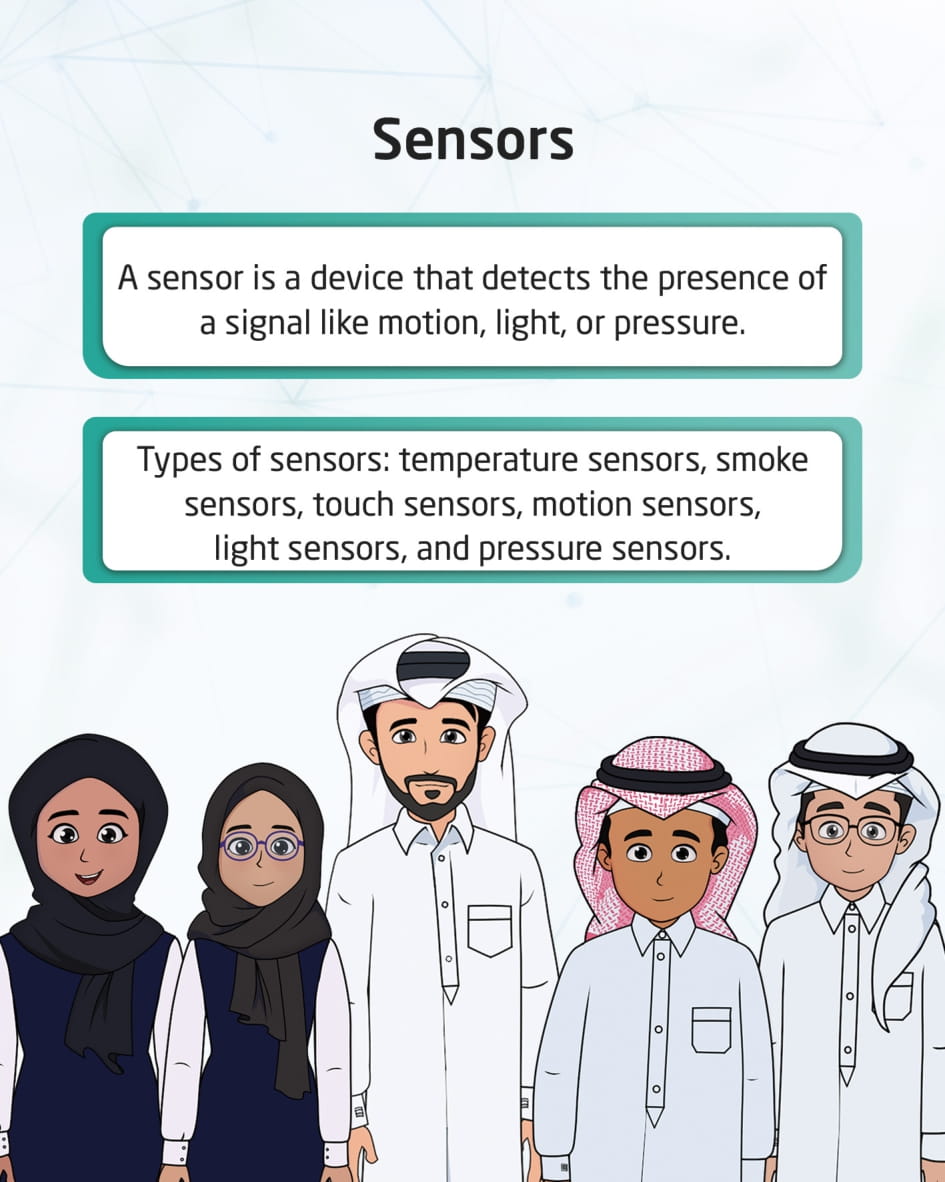
Sensors
This visual content talks about sensors that are used to detect the presence of a signal such as motion, light, pressure, temperature change, etc. There are several types of sensors, including: temperature sensors, smoke sensors, touch sensors, motion sensors, light sensors, and pressure sensors.
WATCH NOW -

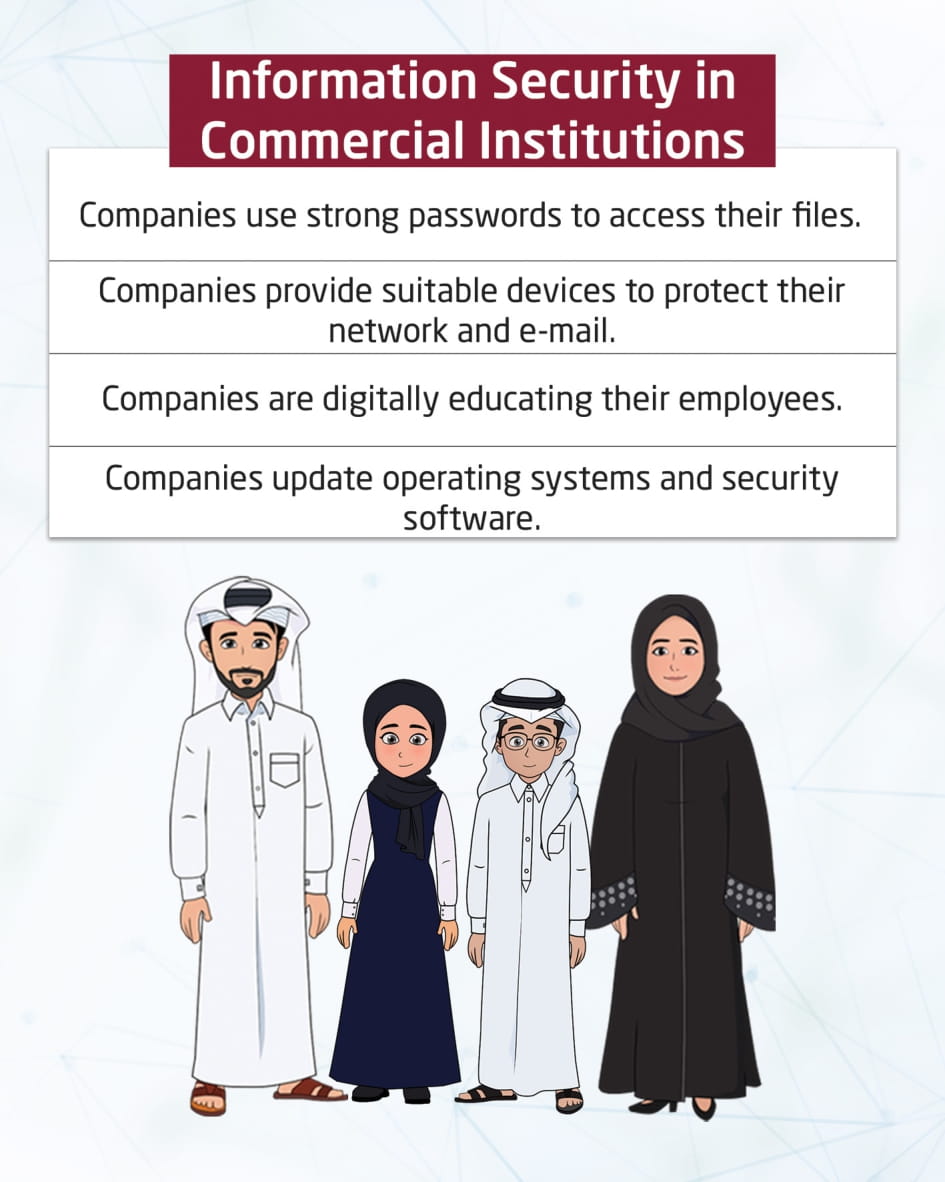
Information Security in Commercial Institutions
This visual content talks about information security in commercial organizations, and that companies use passwords to access files, provide suitable devices to protect the network and e-mail, digitally educate their employees, and work on periodic automatic updates of operating systems and applications, and install protection programs.
WATCH NOW -

Searching and verifying the quality of information
This visual content talks about how to search and check the quality of information on the Internet, and that when collecting information about a specific idea or when visiting a website, the information quality standards must be checked, which include: Accuracy, relevance, timeliness, level of detail, and adequacy.
WATCH NOW -
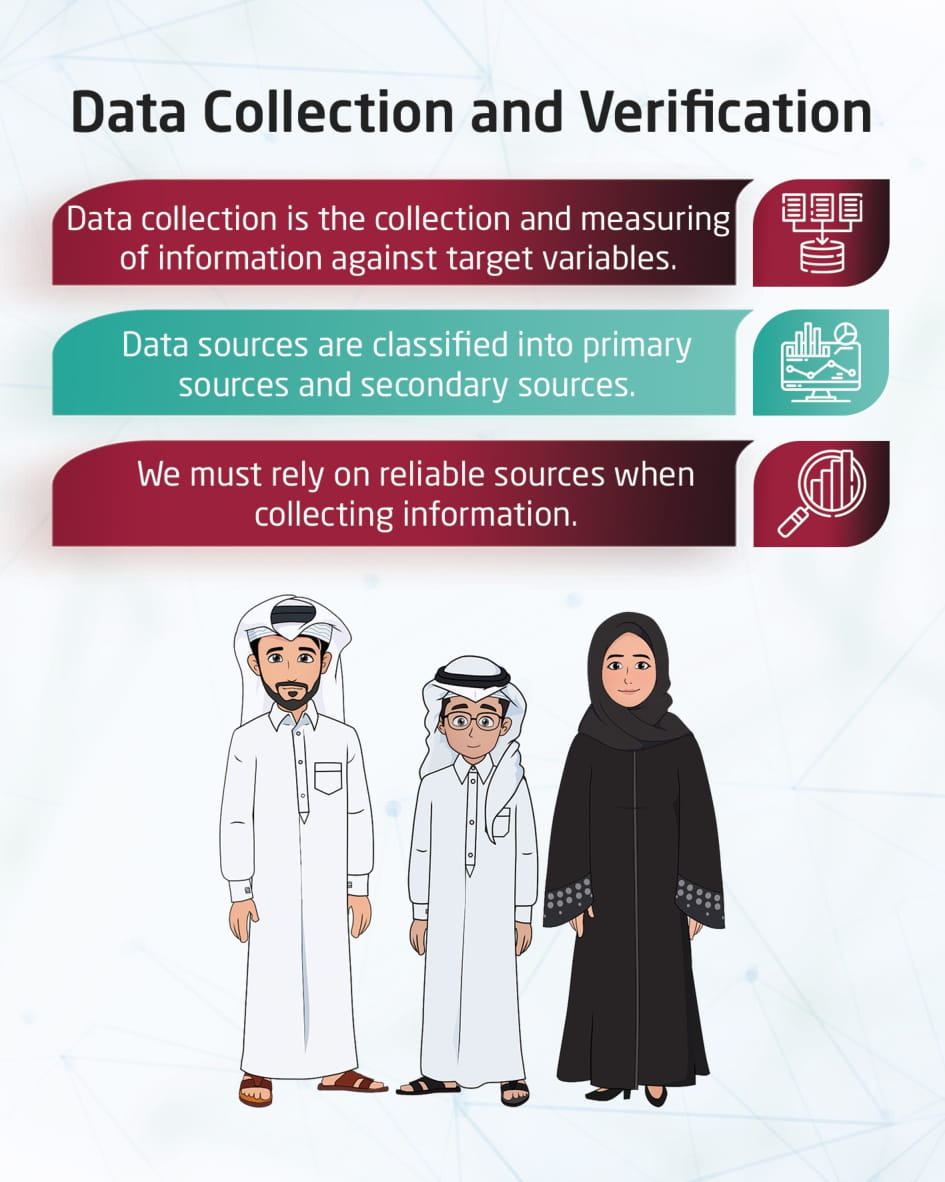
Gathering data and verification
This visual content talks about how to collect data and verify its credibility on the Internet, by having excellent research tools, and relying on reliable data sources.
WATCH NOW -
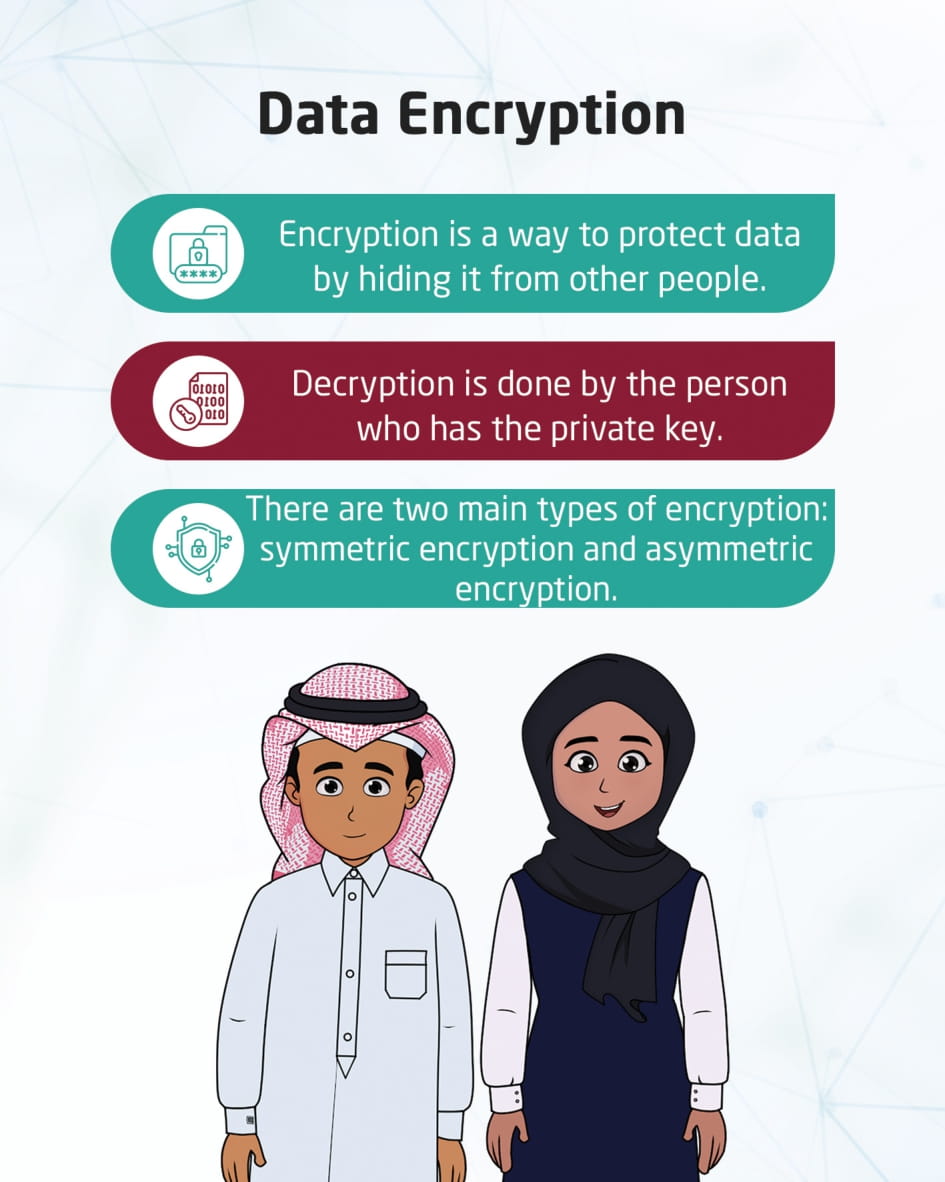
Data Encryption
This visual content talks about a way to protect data by encrypting it and hiding it from unwanted people. So that only the person who has the decryption key can access it. There are two main types of encryptions. They are: Symmetric encryption and asymmetric encryption.
WATCH NOW -

System Design – System Security Issues
This visual content talks about the mechanisms for identifying the elements and components of the system; Through analysis, design, implementation, testing, and then publication. During the design phase, system elements, components, and system interfaces are identified, such as system architecture, hardware components, operating systems, programming, integration with other systems, and system security issues.
WATCH NOW -

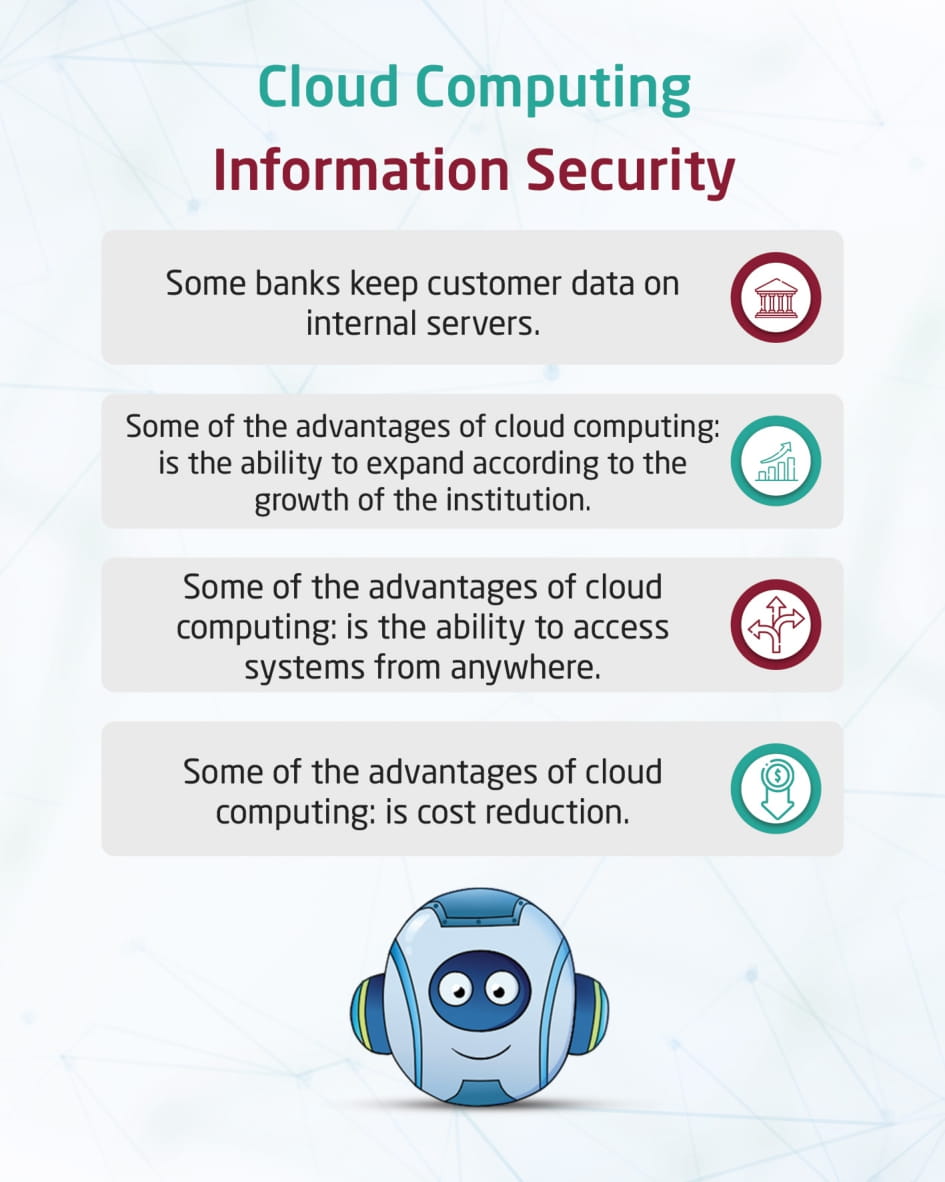
Cloud computing – information security
This visual content talks about the importance of cloud computing and protecting information security. Cloud computing is characterized by the ability to expand according to the growth of the organization, the possibility of accessing systems from anywhere, its lower cost, and the lack of need for technical support and information technology specialists.
WATCH NOW -

Are My Files Safe on Cloud Storage?
This visual content talks about cloud storage, and that it is a technology that provides a safer service for companies to store data instead of traditional computing methods, but care must be taken when moving to the cloud, taking into account data security and adhering to digital security policies, and qualifying employees when moving to cloud computing.
WATCH NOW -
Raspberry Pi Based projects – Digital Surveillance Systems
This visual content talks about digital surveillance systems, and that a smart home is a great example of automation using a Raspberry Pi. In this type of house, it is possible to remotely monitor and control objects and devices that support this technology, and to build a surveillance system using high-resolution cameras.
WATCH NOW -

Researching and verifying Quality of information (Market Study)
This visual content talks about studying the market, collecting and analyzing data and information about a specific market, and the consumers in it, with the aim of knowing consumers’ habits and current needs, and the products that may be popular with them. Therefore, the quality of the information should be ensured through standards of accuracy, relevance, and timing.
WATCH NOW -
Electronic payment methods
This visual content talks about electronic payment methods and online shopping, where it is possible to shop online using tablets and smartphones, and payment can be made upon receiving the product, or through an online payment service such as a credit or debit card, and a bank transfer can be made or by using transfer companies.
WATCH NOW -

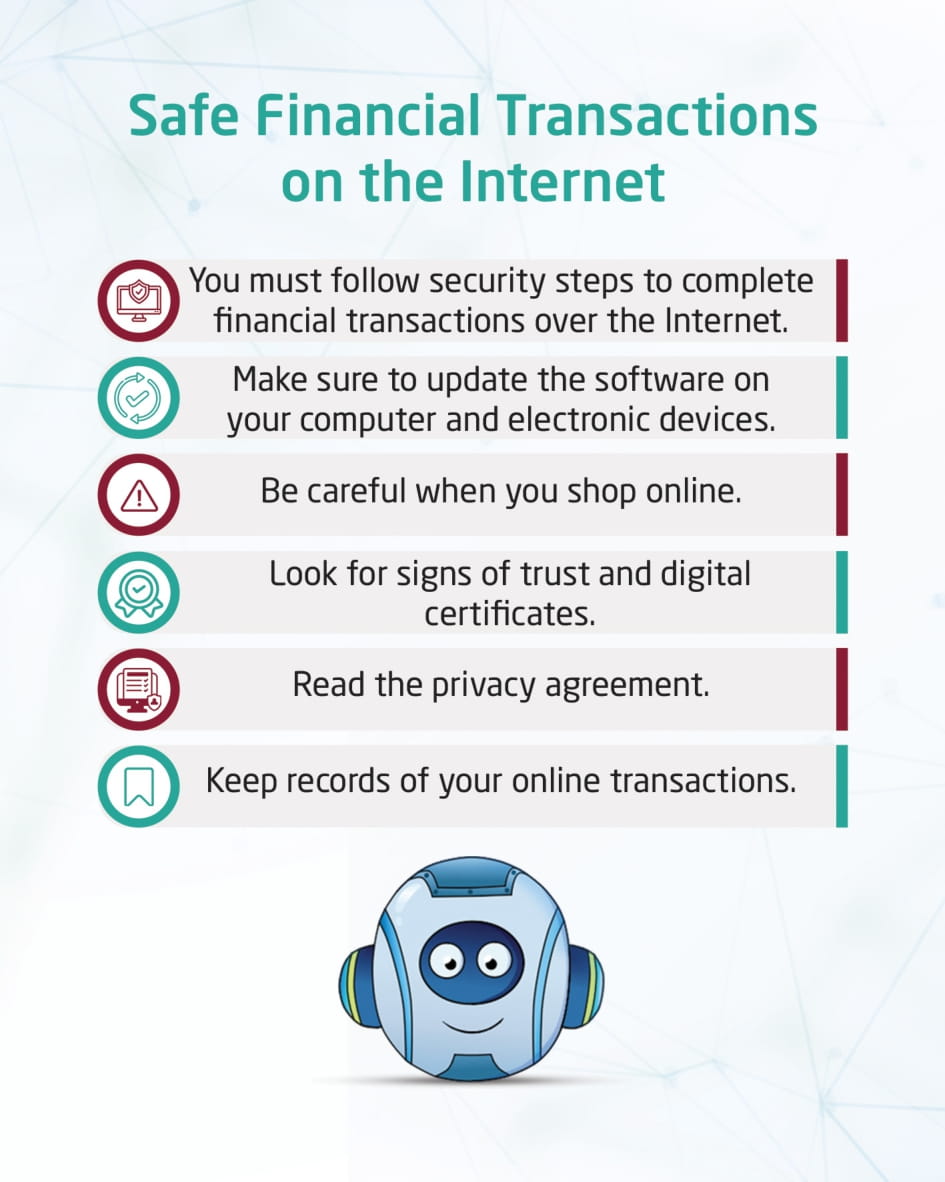
Secure online financial transactions
This visual content talks about secure financial transactions over the Internet, and the need to follow safety steps to complete financial transactions, by updating programs on computers and electronic devices, searching for trust signs and digital certificates, reading the privacy agreement, keeping transaction records, and checking e-mail.
WATCH NOW -

Online fraud
This visual content talks about online scams carried out by fake websites. They offer discounts, have poor design and weak language, limited or suspicious contact options, and URLs on fake sites containing strange words, letters, or unusual domains
WATCH NOW -
Trust Signs and Secure Connection
This visual content is about trust signs and safe connections on the Internet. And that security banners, transaction protection symbols, and trust signs must appear on web pages that request sensitive information. A secure connection is a connection that is encrypted by one or more protocols to ensure the security of data flow between two or more parties on the network.
WATCH NOW -

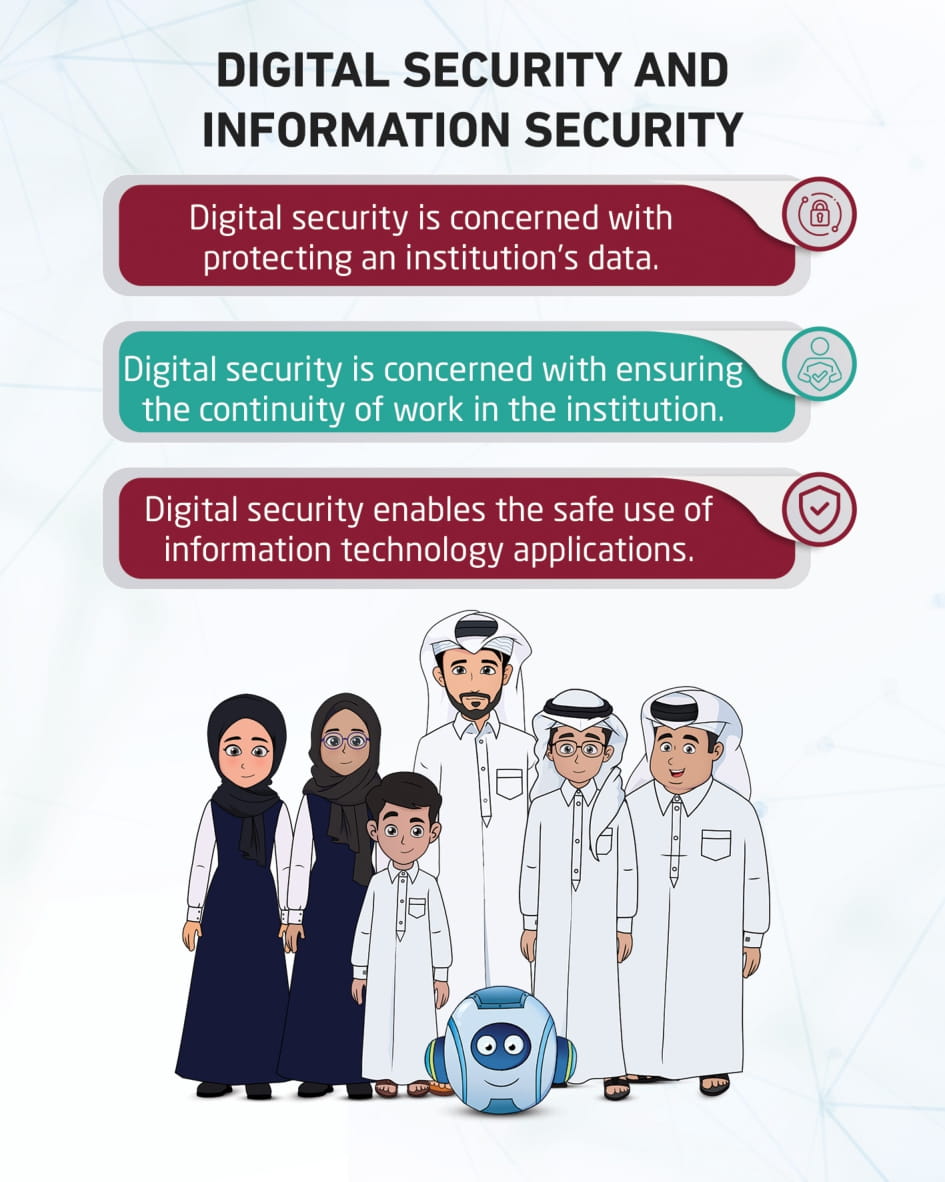
Digital security
This visual content talks about digital security responsible for protecting computers, networks, programs, and data from unauthorized access, and is concerned with protecting enterprise data, everything related to saving and using that data, protecting business continuity in the enterprise, and allowing safe operation of applications built on IT systems in the enterprise.
WATCH NOW -

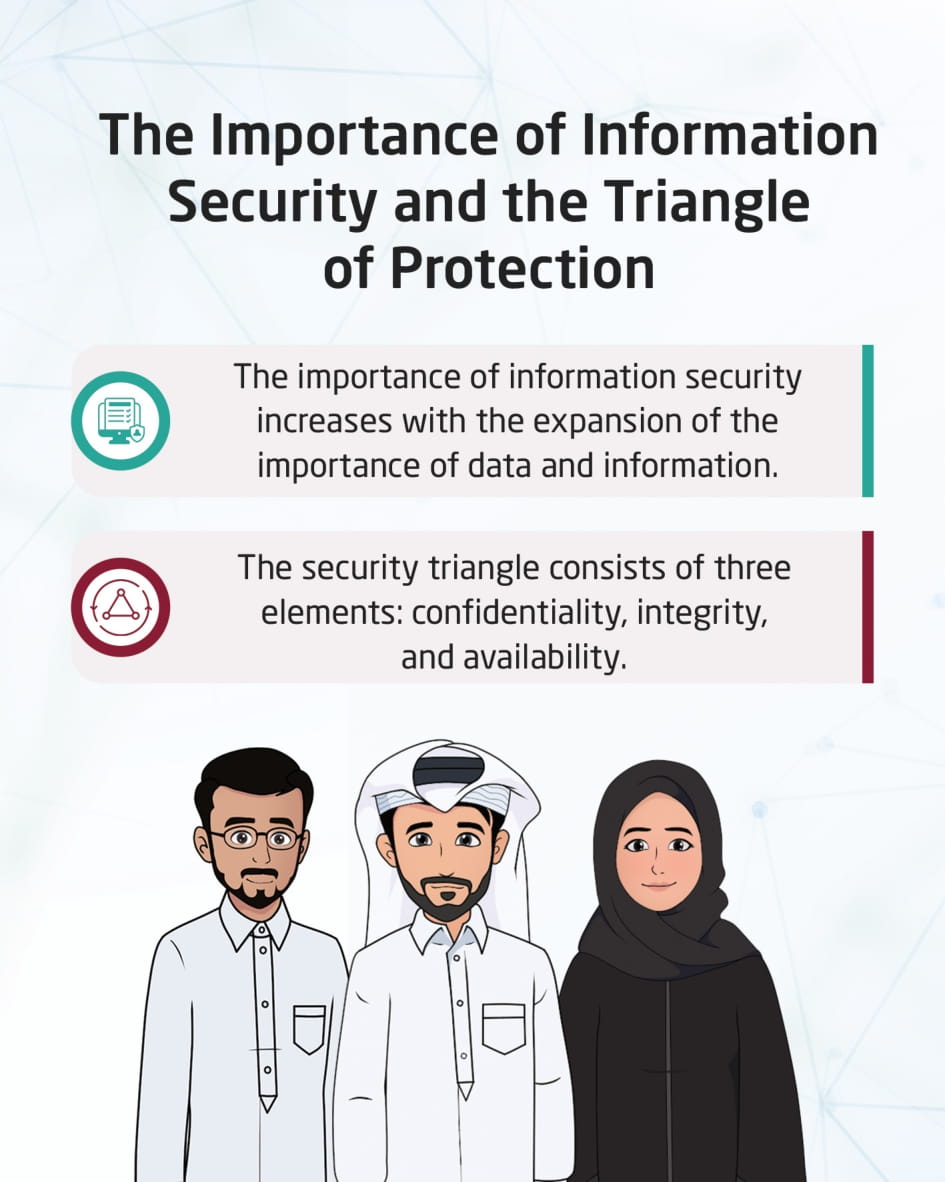
The importance of information security and CIA Triad
This visual content talks about the importance of information security, which increases with the importance of data and information available on the network, and the need for its availability to users without interruption. The CIA Triad consists of three elements: confidentiality, integrity, and availability.
WATCH NOW -
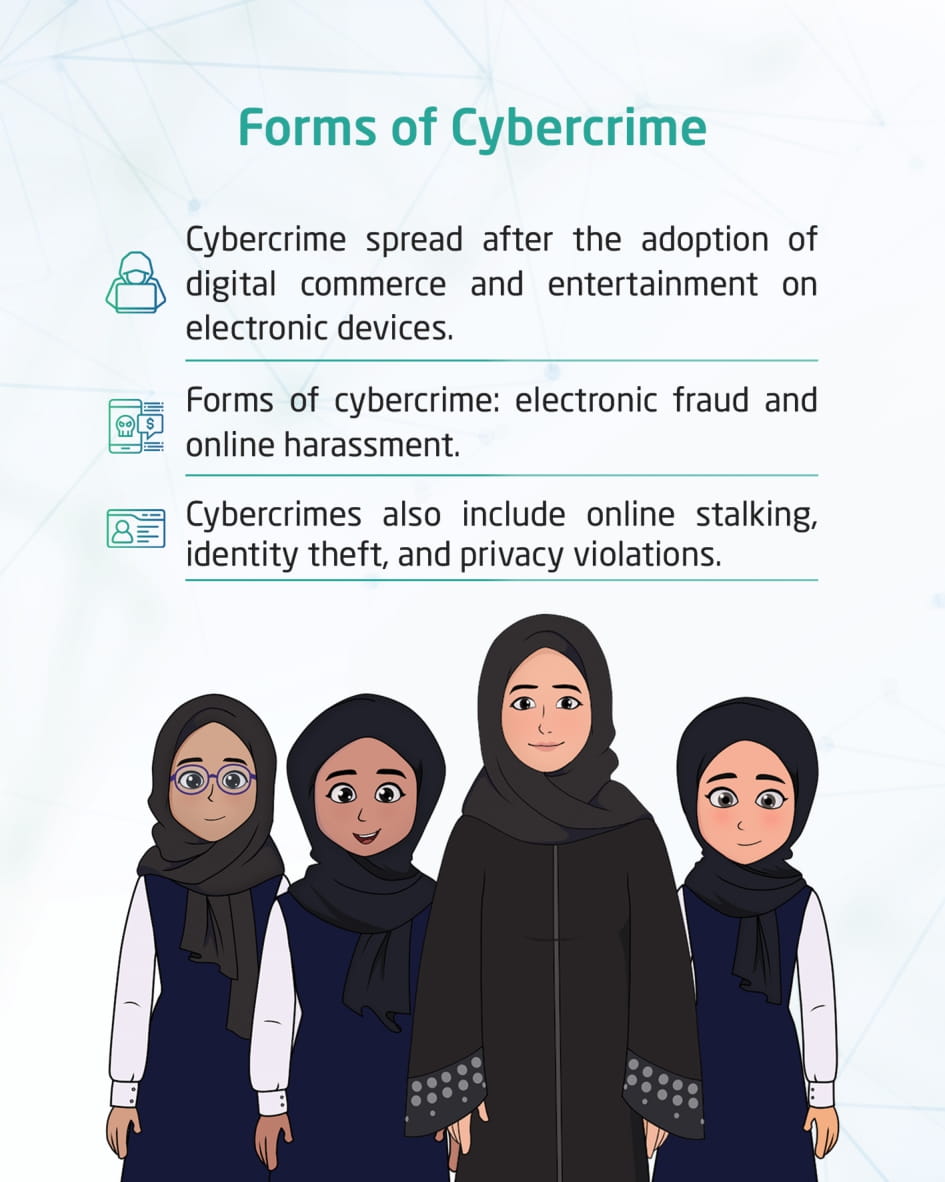
Cybercrimes
This visual content talks about cybercrime and the use of computers to achieve illegal ends. Such as electronic scams, illegal distribution of copyrighted material, identity theft, invasion of privacy, online harassment, or cyber intrusion.
WATCH NOW -

Personal security precautions
This visual content talks about personal security precautions, through regular software updates, the use of antivirus and firewall software, digital communication with caution, the use of strong passwords, in addition to two or multiple verifications, periodic data backup, avoiding using public Wi-Fi networks
WATCH NOW -
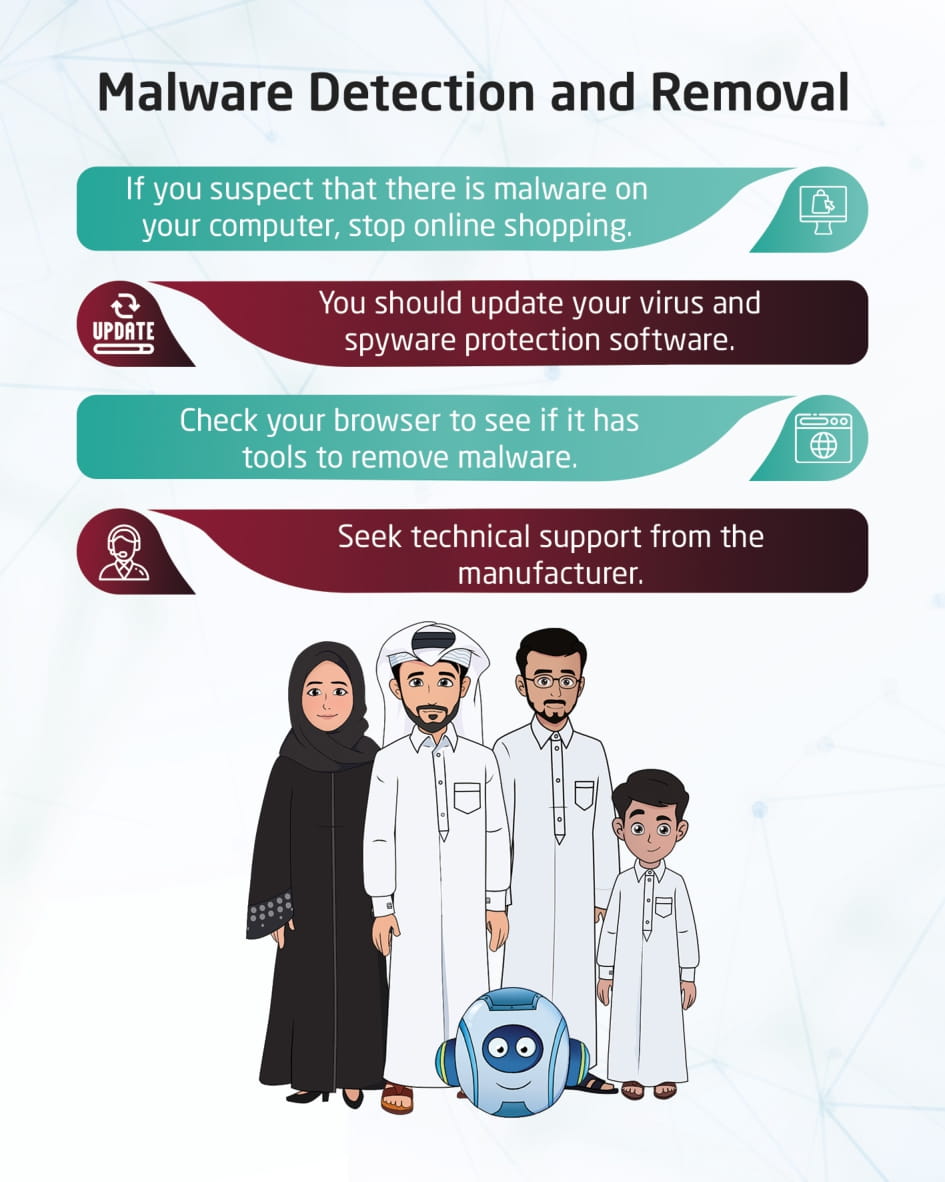
Detection and removal of malware
This visual content talks about the detection and removal of malicious software, and when you suspect the presence of any malicious software, you should stop online shopping and banking services on the computer, update your antivirus software, scan your computer for viruses and spyware, check your browser, and seek support.
WATCH NOW -
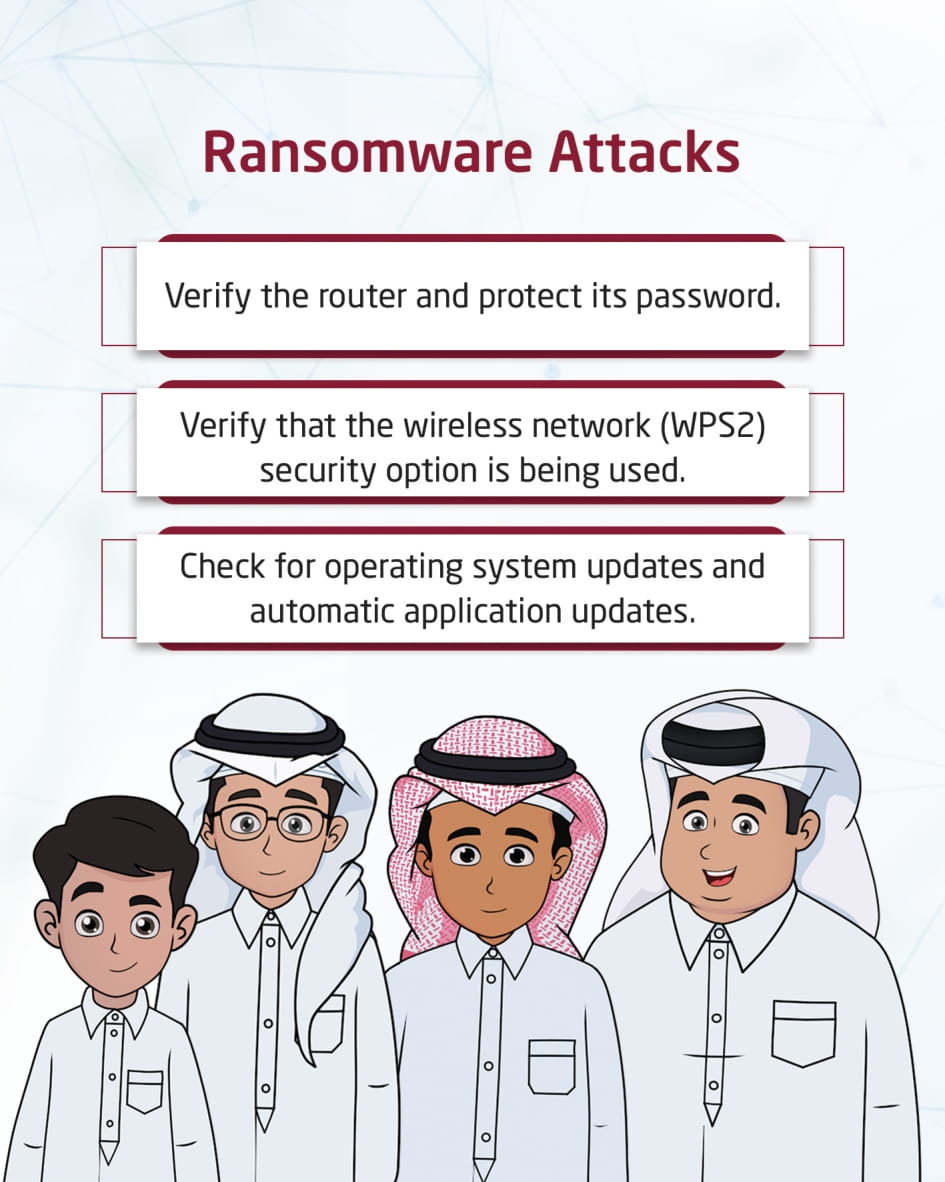
Ransomware attack
This visual content talks about ransomware attacks and how to protect electronic devices from it by checking the router, protecting its password, using a security option for the wireless network, checking for updates of the operating system and applications, checking the firewall, and backing up important data.
WATCH NOW -

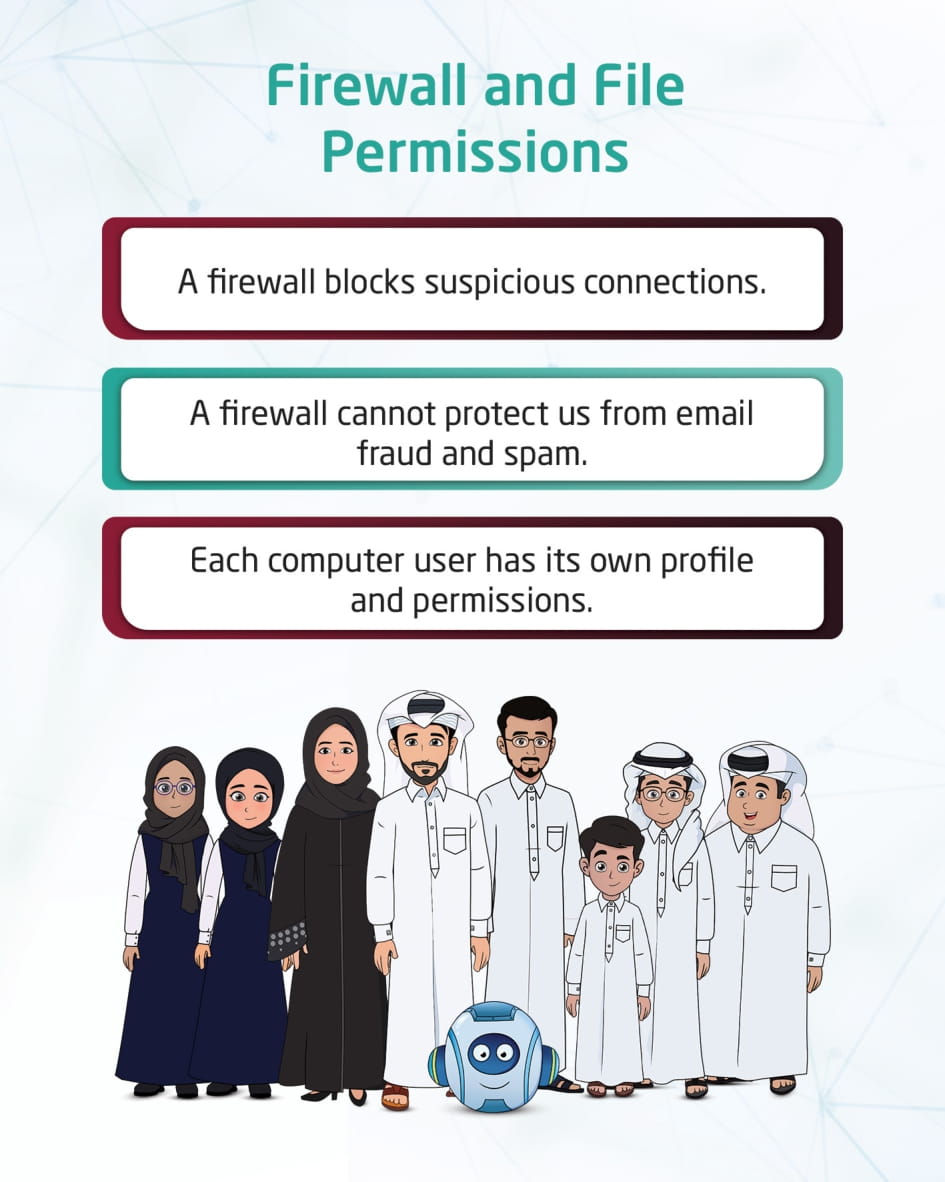
Firewall
This visual content talks about the firewall, which is software or hardware used for network security, that controls incoming and outgoing traffic by analyzing the data packets and determining whether they should be allowed through or not. A firewall blocks suspicious connections, but it does not protect against email fraud, ads, and spam.
WATCH NOW -

File and folder permissions
This visual content discusses permissions for files and folders. It explains that, depending on what we want others to be able to control, we use a variety of permissions to safeguard our files and folders. One of the most significant categories of permissions: is complete control, modification, reading, and execution, as well as viewing, reading, and writing folder contents.
WATCH NOW -

Digital footprint
This visual content talks about our digital footprint, which is how we browse, communicate, and do other things online. They are two types: the active digital footprint we leave of our own free will, like our publications on communication sites and subscriptions to electronic lists, and the unknown digital footprint we leave unintentionally; Such as applications and sites that determine our geographical location.
WATCH NOW -
Effects of digital tracking
This visual content talks about digital tracking, and that every action or browsing we do on the Internet leaves a trace called a digital footprint, which others may be able to see, such as browsing history, the sites we visit, and websites saving some information in storage memory and cookies.
WATCH NOW -

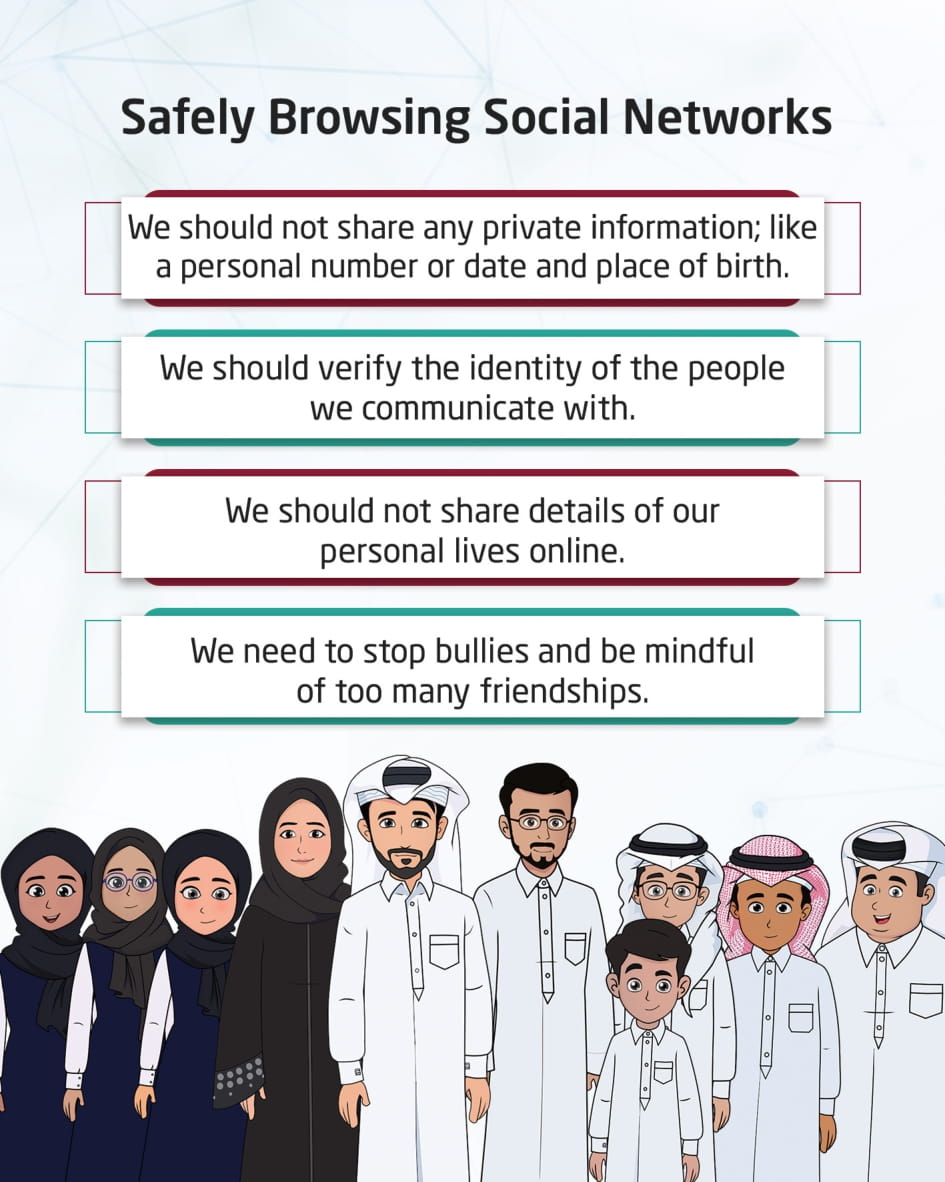
Safe browsing of social networks
This visual content discusses being cautious when browsing social networks, not sharing any private information, adjusting privacy settings, verifying the identity of people with whom we communicate so that they cannot see the content we share, using strong passwords, avoiding bullies, and being cautious about a number of excessive friendships.
WATCH NOW -

Cybersecurity
This visual content discusses the fact that Cyber Security is a system for protecting computer systems directly connected to the Internet from any electronic attacks that could result in identity theft, attempts at blackmail, and the loss of important data. It also protects data and programs from these attacks. As a result, Cyber Security regulations that guard against cybercrime must be adhered to and data must be safeguarded
WATCH NOW