In the curricula for middle school students, educational content was developed in line with the expansion of the child's perceptions, knowledge, and ability of absorption, analysis, and comprehension. The educational content at this stage is complementary to the content in the elementary stage and is based on information related to computing and information technology, how to deal with social networking sites, websites, and other relevant information.
In this stage of the curriculum, new, age-appropriate characters were introduced and created to give the films an air of fun and increase suspense and attraction in them.
-

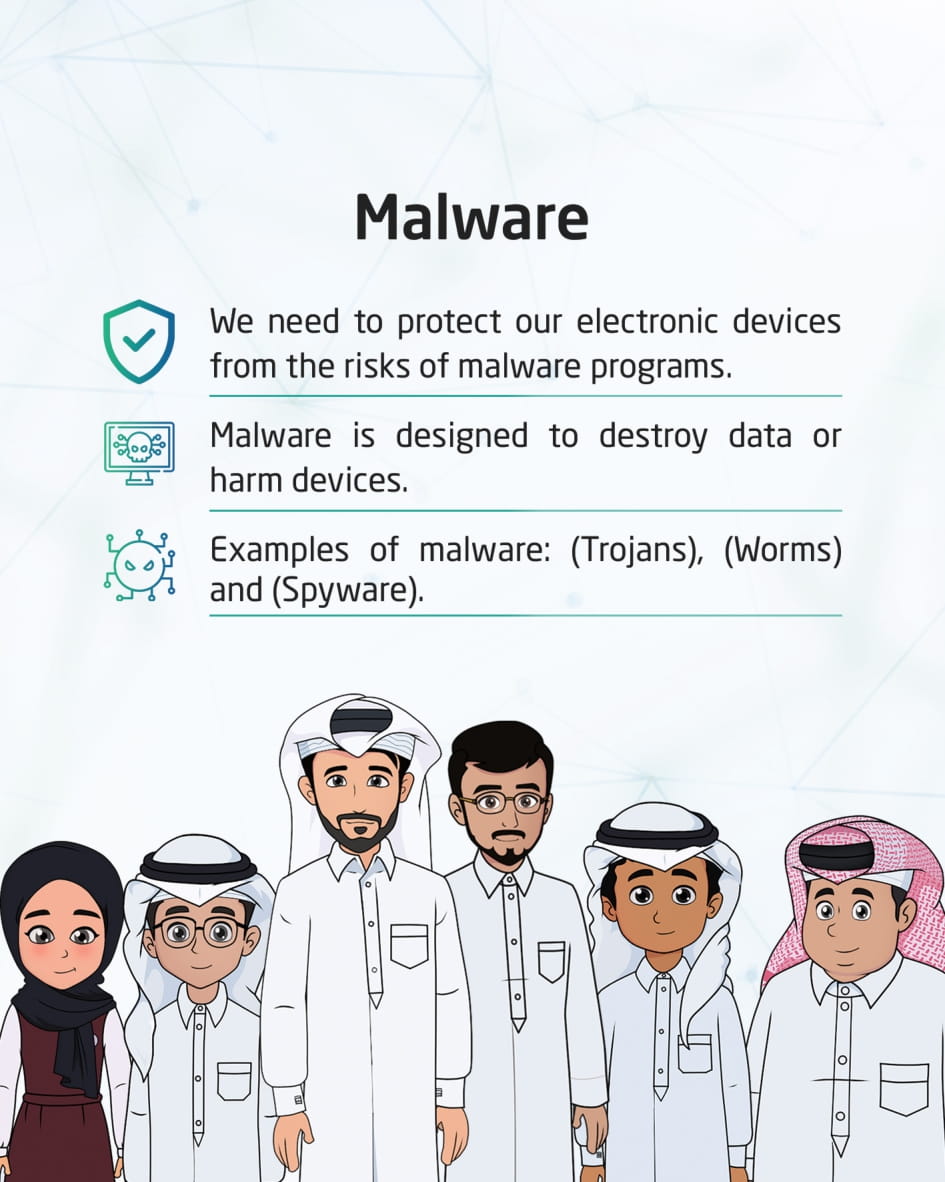
Network Protection from Malware
By not revealing the username or password, not opening emails from unknown sources, creating strong passwords, periodically changing them, avoiding suspicious websites, and updating an anti-virus program, this visual content discusses ways to protect network-connected electronic devices from malicious programs and viruses.
WATCH NOW -

Social Media networks/ Part one
This visual content discusses the benefits of social media, including the fact that it makes it possible to communicate with people all over the world, facilitates the exchange of ideas with other people, makes it easier to access news and information, and aids in e-marketing and business operations.
WATCH NOW -

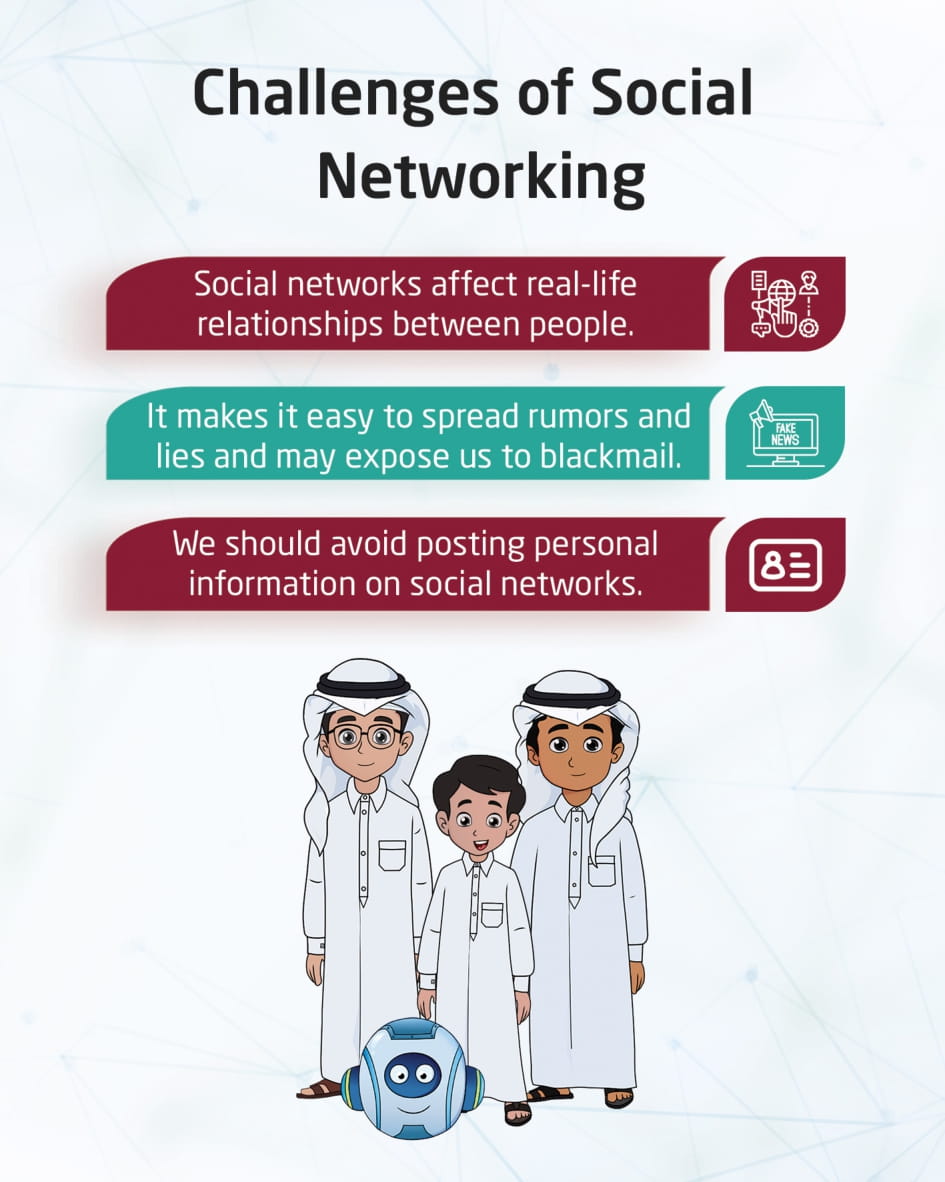
Social Media networks Challenges
This visual content discusses social media’s difficulties, as it has an impact on real relationships, wastes time, encourages the spread of rumors, and has the potential to put its users at risk for cyberbullying, data theft, and privacy violations.
WATCH NOW -

Computer Protection Procedures
This visual substance discusses methods for safeguarding the computer by installing antivirus programs on it, and regularly updating it so that you detect new malware, and avoid closing the firewall because network loopholes are the target of viruses.
WATCH NOW -

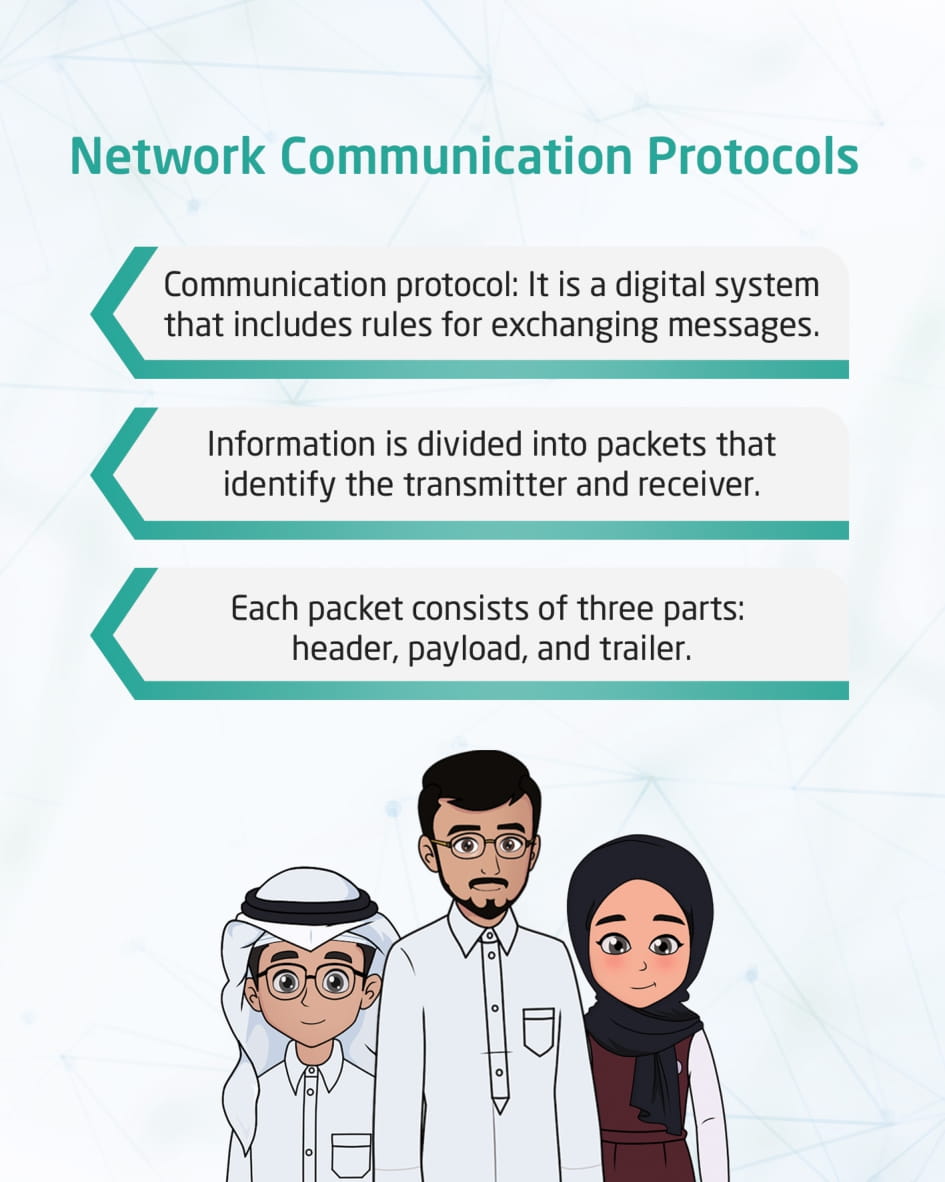
Communication Protocols in Networks
This visual content deals with the communication protocol in networks, which is a digital system that includes rules for exchanging messages. to ensure that it arrives properly; Where the information is divided into packages in which the transmitter and receiver are identified so that a confirmation is sent to the sender when the packet is received by the receiver. When the packet is lost, it is retransmitted again.
WATCH NOW -

Data Privacy
This visual content talks about the importance of preserving data privacy, and not giving personal data to anyone over the Internet. Because this may involve the risk of exposing the person to theft. Therefore, it is necessary to refrain from sharing personal information with others.
WATCH NOW -

Children’s Personal Information
This visual content talks about the necessity of preserving children’s data and not disclosing it so that they are not exposed to abuse, and the necessity of reading the privacy statement that explains the type of information and the reason for its request, and where it will be used.
WATCH NOW -
Backup and database protection
This visual content talks about protecting databases by making backup copies, and placing them in a secure, protected system that can be accessed when needed. Backups can be stored on an online storage account or on various external storage media.
WATCH NOW -

Backup and database protection with the password
This video talks about protecting databases and backups with strong passwords, to provide protection for files and data. When setting the password for the database, it must be opened in Exclusive Mode.
WATCH NOW -

Online Meetings
This video talks about online meetings, where a remote meeting can be held via the Internet, which allows many details to be shared through it, such as files, data, and presentations. There are modern applications that have been employed for this purpose, such as Zoom.
WATCH NOW -

Best practices for working online
This visual content talks about best practices for working online, adherence to proper procedures to reach the best results, sharing information with caution, being mindful of potential hardships such as different languages and cultures, and avoiding sharing personal information with strangers.
WATCH NOW